Arbitrum生态又有好项目诞生?Rari Chain宣布上线
Arbitrum无疑是近段时间以来最热的Layer2公链,它衍生出了许多优质的项目,如游戏专用链Xai、公共测试网Nitrogen(AltLayer)、固定收益应用Meliora以及符合KYC标准的Layer2网络Kinto。
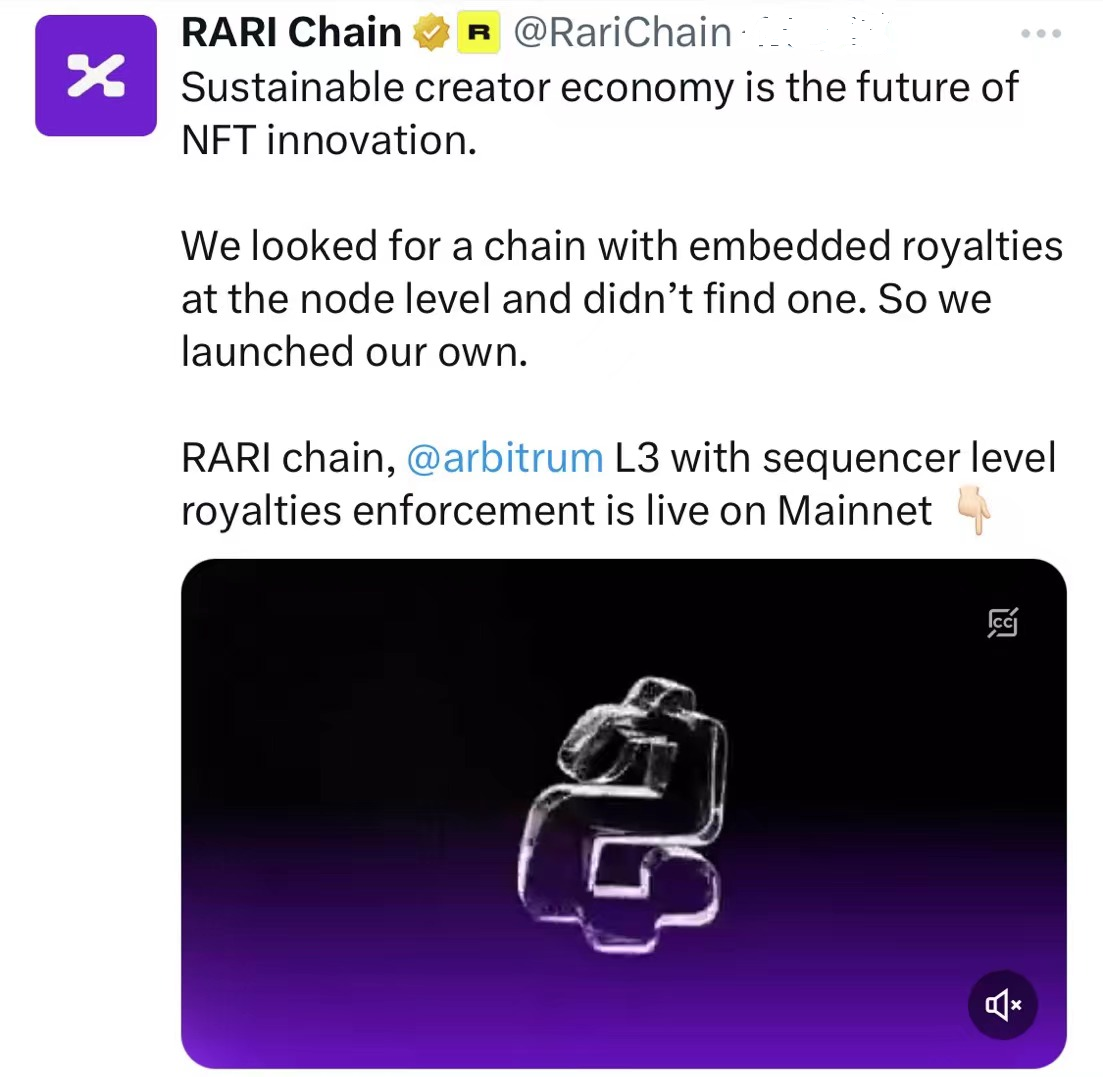
2024年1月24日,Rari Foundation代表Rari DAO在Arbitrum上推出Rari Chain主网,这也再次引发了市场的关注。
Web3世界的朋友圈不断扩大,Rari Chain的吸引力得以充分展现
在正式介绍Rari项目之前,我们不妨了解一下它近期的合作动态。
近期,Rari Foundation还与包括Caldera、Gelato、LayerZero、Magic、Rarible、Thirdweb和WalletConnect等在内的行业领先企业建立了合作关系,这也从侧面反映出Rari对于外部力量的吸引力。
近乎同一时间,跨链互操作性协议LayerZero宣布上线Rari Chain,这意味着与LayerZero集成的应用程序现在可以将RARI Chain添加为支持网络之一。RARI Chain的生态系统变得更加多元,创作者和开发者可以通过LayerZero端点连接超过45条公链,这为他们提供了更广泛的选择空间和更灵活的应用场景。
另外,GALXE也在其官网上推出了与Rari Chain相关的任务,以庆祝Rari Chain的发布。这些任务允许参与者赚取积分,并有机会获得$RARI代币等奖励。这一举措展示了加密货币社区对Rari Chain的兴趣和积极参与,也为更多人提供了参与加密货币生态系统的机会。
下文将为读者介绍下Rari Chain这个项目。
Rari Chain的差异化特性:允许用户低成本铸造、交易NFT,支持多种编程语言
Rari Chain是一个基于Arbitrum的EVM等价链,专注于通过节点级别的版税嵌入机制来保护NFT版权。作为一条Layer 3链,它不仅增强了Arbitrum的扩展性,还为NFT生态系统提供了额外的功能。自2023年11月30日测试网推出以来,其吸引了约46,000个钱包地址参与,完成了超过251,000次交易。RARI Chain的内置版税功能,允许用户为每个NFT或整个系列定制版税比例。如今,Rarible正在努力将RARI Chain整合进其Rarible协议和Rarible X平台,进一步扩大Rari Chain的应用范围和影响力。
Rari Chain在交易成本和速度方面进行了重大优化。用户可以以极低的成本创建、铸造和交易NFT,同时Gas费用在与NFT交互时几乎不再是考虑因素。此外,Rari Chain支持通过信用卡支付ETH、USDC或美元,无需桥接,实现快速灵活的支付体验。
Rari Chain坚持“社区第一”的原则,与Rarible市场紧密集成,并由RARI DAO社区管理,确保多元化和包容性。在NFT应用构建方面,Rari Chain作为Ethereum L3链,继承了Ethereum的安全性,同时提供低交易成本和快速区块确认时间。它支持ERC-721和ERC-1155合约的NFT交易,并通过版税执行检查机制,确保版税的有效支付。
Rari Chain支持多种编程语言,允许开发者使用Rust、C和C++等编写EVM兼容的智能合约。它的强大兼容性为用户提供了广泛的选择空间。同时,Rari Chain鼓励开发者和创作者探索新的使用案例,如链上存储NFT、游戏内NFT交易或数字与实物NFT的结合。为早期采用者提供的资助计划进一步激发了创新和参与热情。
上线主网只是第一步,Rari Chain的未开仍然充满不确定性
当然,随着加密货币领域的不断发展,竞争也变得日益激烈。Rari Chain虽然迎来了成功的发布,但其未来依然充满挑战和不确定性。其生态系统的发展将取决于用户的采用程度以及与合作伙伴的合作成果。加密货币市场一直在快速变化,因此Rari Chain需要不断创新和适应市场需求,以保持竞争力。我们期待看到Rari Chain如何在未来的时间里塑造加密货币领域,并为开发者和用户带来更多的机会和创新。